No Equal
Vulnerability Management
Our team combines deep expertise in cybersecurity with a commitment to tailoring solutions to your unique needs, ensuring proactive protection against evolving threats while minimizing the burden on your organization.
- Virtual Scanner:
- No hardware needed. Our appliance scans and identifies vulnerabilities with Six Sigma (99.99966%) accuracy, protecting your IT assets on premises, and the cloud.
- Endpoint Agents:
- Unlock the full power of vulnerability detection with our endpoint agents. A continuous and indepth scan of your workstations and servers will take place yielding a trove of vulnerability data.
- Constant Monitoring:
- We setup alerting about potential threats so problems can be addressed before turning into breaches.
- Theatfeed:
- We track Zero Day exploits so you do not have to. We stay up date on the latest exploits and automatically scan your environment searching for any indication of their existance.
- Patch management and Remediation:
- Blue Solis Technology has experts fully capable of running an entire patch program from the ground up.
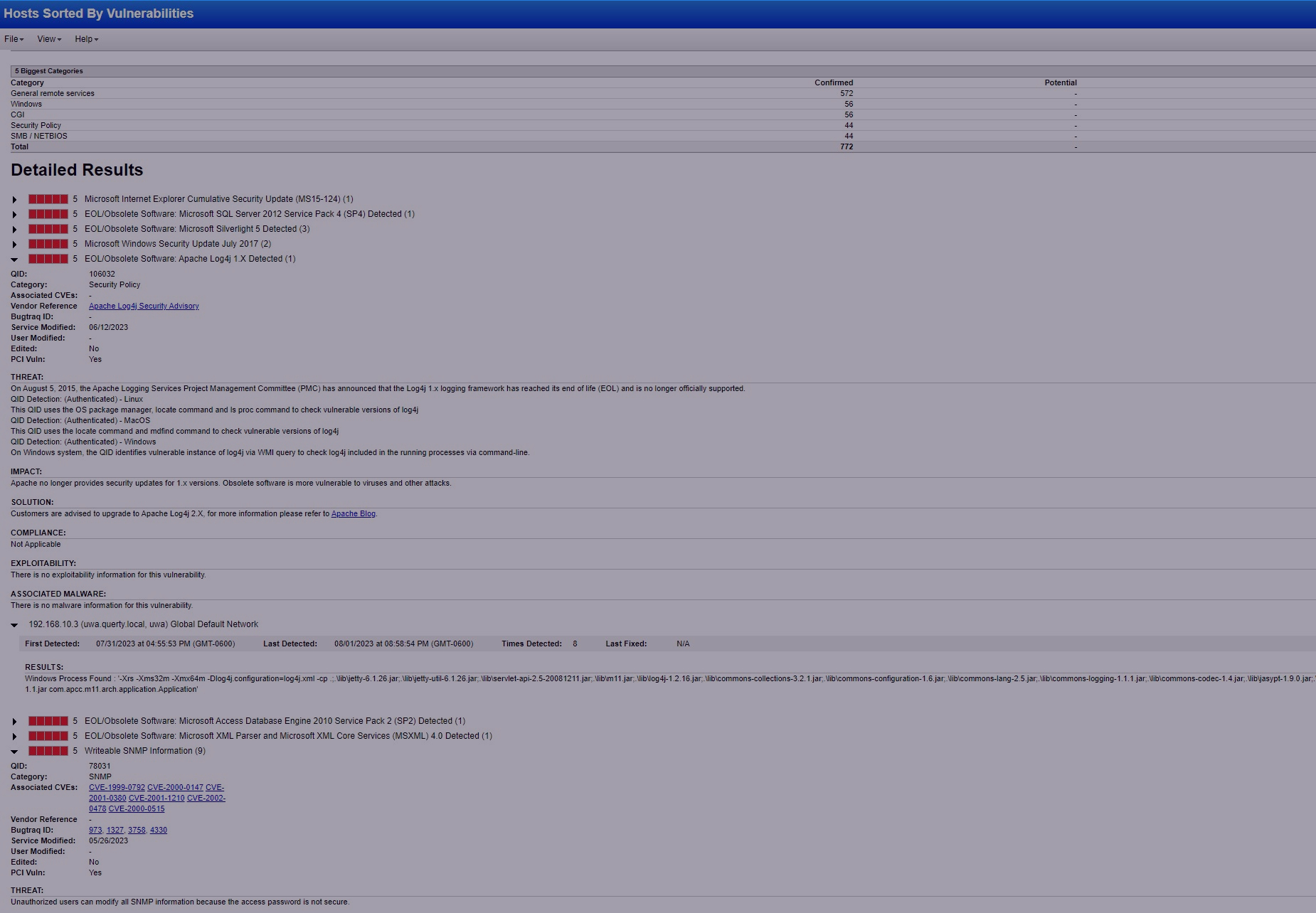
- Powerful Reporting:
- Securly receive reporting, daily, weekly or monthly on the status of your organization.
Our Process
From Beginning To End
The industry’s most advanced, scalable and extensible solution for continuous vulnerability management
- Discovery:
- Swiftly ascertain the active components across various segments of your network, spanning from the perimeter network to virtualized machines and beyond.
- Scan for vulnerabilities:
- We scan everything in your network, if it has an IP address, we find it.
- Identify and prioritize risks:
- We identify the highest business risks using trend analysis, Zero-Day and Patch impact predictions.
- Remediate vulnerabilities:
- Once the vulnerabilities are identified and prioritized its off to the races to remediate.
- Reporting:
- Reports are generated on demand or scheduled automatically and then shared with the appropriate recipients online, in PDF or CSV
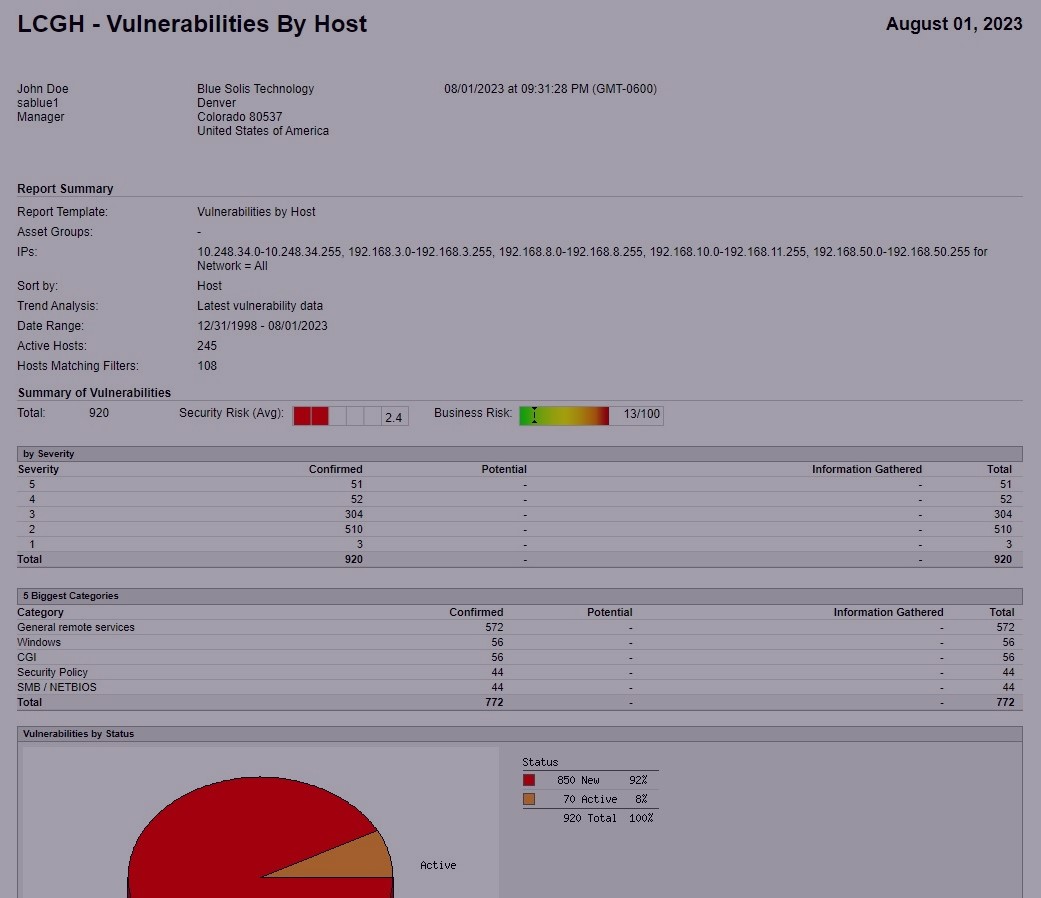
Patch Management
Our patch management will save your organization time and money. We support many different technologies and have extensive experience managing patches and their many complexities.
-
Cloud Agents
Our cloud agents are installed on your endpoints through an automated process so no devices are missed.
-
Attention to Detail
We assess which assets need to be prioritized and draft a patching schedule.
-
Plan and Execute
Patches are sent out to your assets in a scheduled and controlled manner, minimizing complications.
Vulnerability Management Breakdown
Our vulnerability management offering not only proactively identifies and mitigates security weaknesses but also seamlessly integrates with our EDR/XDR solutions, enhancing their robustness and equipping organizations with a comprehensive security ecosystem.
Inventory Assets
- Discover Assets
- Inventory Assets
- Asset Specifics & Data Capture
- Device & Software End of Life Audit (Add-On)
Vulnerability Management
- Constant Vulnerability Scanning
- Asset Configuration Assessment
- Certificate Assessment
- Mobile Device Vulnerability & Misconfiguration Assessment (Add-On)
- Cloud Security Assessment (Add-On)
- Container Security Assessment (Add-On)
Threat Detection & Prioritization
- Continuous Monitoring
- Threat Protection - Leveraging real-time threat intelligence from CISA
Threat Response
- Patch Detection
- Patching Via Cloud Agent (Add-On)
- Patch Management for Mobile Devices (Add-On)
- Device & Software End of Life Audit (Add-On)

Let's Meet
Our 30 minute consultations are a great place to meet, ask questions and ensure we are right for you.
- Vulnerability Management
- Policy Compliance
- Composed of Experts
- Patch Management
- Annual Agreements
- Scalable Solution
Commission Your Security
Review our industry leading offerings and secure your organization