Multi-Vector Endpoint Detection and Response
With support for Window, Mac and Linux, having more than a simple antivirus is crucial. Endpoint Detection and Response (EDR) solutions provide the essential capability to not just detect and prevent malware but also proactively hunt advanced threats, offering a comprehensive defense strategy to safeguard critical systems and data.
- Built-in anti-malware technology:
- Multiple layers of protection against malware, phishing, and exploits, augmented by application behavior scanning, ensuring precise identification and automatic blocking of any malicious attacks on the endpoint within seconds
- Continuous vulnerability detection:
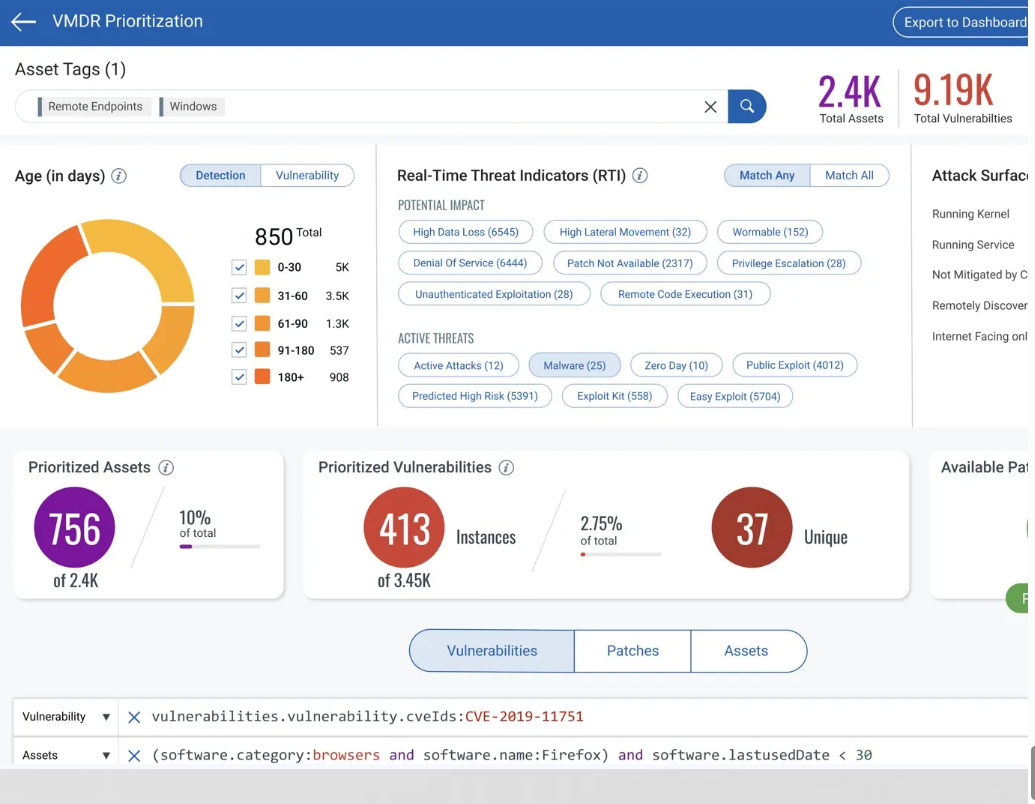
- Have your EDR do more for you with additional capabilities like vulnerability scanning, misconfiguration detection and patch management.
- Real-time visibility into asset inventory and telemetry:
- Provides extensive insight into endpoint telemetry, including hardware and software specifics, version information, end-of-life status, usage history, licensing, geographic location, running services, processes, open ports, and valuable network traffic data.
Multi-Vector EDR
Our EDR solution has powerful capabilities and tons of additions
Pre Attack Prevention
EDR agents demonstrate exceptional resilience by seamlessly and effectively countering threats while maintaining system performance
What’s included
- Anti-malware
- Randsomware Attacks
- File-less Attacks
- Exploit Blocking
- Anti-Phishing
- Behavior-based Attacks
- Asset Dicovery and Inventory
- Vulnerability Management (AO)
- Misconfiguration Assessment (AO)
- Patch Management (AO)
Resiliance and Performance
Addon options are denoted with (AO)
Gone are the days of several software installations. All of these capabilities come from ONE endpoint agent.
Breach Detection
EDR agents excel in rapid breach detection, swiftly identifying and mitigating security incidents to safeguard critical systems and data
What’s included
- MITRE Attack Techniques and Tactics-Driven Detections
- File, Process & Registry Events
- Memory Scan
- Threat Intelligence
- Insights Into Open Ports, Running Processes, Services & Installed Software
- File Integrity Monitoring (AO)
- Exploitable Vulnerabilities (AO)
- Exploitable Misconfigurations (AO)
Powerful Capabilities
Addon options are denoted with (AO)
Gone are the days of several software installations. All of these capabilities come from ONE endpoint agent.
Post Breach Reponse
EDR offers robust post-breach capabilities, which effectively contain security incidents, minimizing the impact and facilitating rapid recovery
What’s included
- File Quarantine/Deletion
- Process Termination
- Endpoint Containment
- Configuration Remediation (AO)
- Unwanted Software & Service Removal (AO)
- Defined Automated Response (AO)
All-In-One Agent
Addon options are denoted with (AO)
Gone are the days of several software installations. All of these capabilities come from ONE endpoint agent.

"Multivector EDR/XDR is a formidable cybersecurity solution that combines advanced endpoint detection and response capabilities with a multi-dimensional approach to threat mitigation. Its integrated features, such as threat hunting, behavioral analysis, and real-time threat intelligence, make it a powerful and comprehensive tool for organizations seeking robust protection against a wide range of cyber threats."
One Cloud Agent Many Options
Advanced EDR/XDR to End Point Protection we have you covered
We have combined our EDR and XDR solution to provide superior endpoint protection.
Have a question on our EDR/XDR Contact Us
EPP
End Point Protection
- Signature and heuristic-based Threat prevention
- Root cause analysis for malware
EDR (Now Combined with XDR)
Endpoint Detection and Response
- Threat Prevention, Detection and Response
- Signatrue and heuristic based threat prevention
- Zero-day threat coverage
- Suspicious activity detection and response
- Identifies unmanaged, unprotected assets
- Extended coverage includes VMs, containers and IoT
- Full VM integration
- Root Cause Analysis
- For malware
- For endpoints
- Automated Remediation Pathways
- We audit misconfiguraions and pinpoint CVE's
- Proactive Threat Hunting and Hardening
- Searches for indicators of attacks and threats
- Automatic patching solution
- Asset criticality rating and risk-based security
XDR
eXtended Detection and Response
- Threat Prevention, Detection and Response
- Signatrue and heuristic based threat prevention
- Zero-day threat coverage
- Suspicious activity detection and response
- Identifies unmanaged, unprotected assets
- Extended coverage includes VMs, containers and IoT
- Full VM integration
- Root Cause Analysis
- For malware
- For endpoints
- Automated Remediation Pathways
- We audit misconfiguraions and pinpoint CVE's
- Proactive Threat Hunting and Hardening
- Searches for indicators of attacks and threats
- Automatic patching solution
- Asset criticality rating and risk-based security
- Security Orchestration and Response (SOAR)
- Automated alerts
- Streamlines remediation pathways
- Custom workflow reponse triggers

Let's Meet
Our 30 minute consultations are a great place to meet, ask questions and ensure we are right for you.
- Vulnerability Management
- Policy Compliance
- Composed of Experts
- Patch Management
- Annual Agreements
- Scalable Solution
Commission Your Security
Review our industry leading offerings and secure your organization